I struggled to name this blog, as I have long considered the end state an “Application Dictionary”–which would describe your applications and how they connect to each other. However, the intention of the Application Dictionary is to reasonably maintain your security posture with a proper Source of Truth (SoT).
At NTC, we frequently get questions about how best to manage firewall policies from our customers. With the introduction of micro segmentation and zero-trust security models, the problem is only being exacerbated. Like many issues within the network automation space, the underlying cause usually has to do with SoT. Outside of SoT, other issues we’ve seen include:
These issues can ultimately lead to an unfavorable experience overall. The requestor feels that their application should “just work”,the engineer fielding the request wished the requester understood their requests better, and the approver is attempting to ensure security integrity. Ultimately, everyone feels as if the other side “should do more.”
With modern applications, there is no longer the concept of just servers, virtual machines, and L3 separation. Containers and hypervisor separation now blur the lines of security control. What was traditionally handled by systems communicating over the wire via IP can now be controlled by container or hypervisor network and security constructs.
However, in moving in this direction, the centralized control and visibility that once lived in the firewall is lost–when the network or security team does not have access to the container security controls, as an example. In practice, these rules end up getting duplicated due to that lack of visibility, by also creating the rules on firewalls as well.
A non-exhaustive list of complications includes:
I am proposing to introduce what I have dubbed the “Application Dictionary.” This method allows users to speak, such as “I need SNMP monitoring” or “I need my application server to speak to my database,” while also understanding that all of the onus is not on the network/security engineer. There needs to be shared ownership and responsibility overall. That means that requestors, implementors, and approvers all need to have skin in the game.
The basic premise is “everything is an application.” Access between systems is assigned an owner and rules are pushed to the edge. So how does that manifest itself as security controls? Creating a disaggregation from the SoT and the configuration management gives you the ability to express your configurations as near natural language.
If application owners can define their applications as services that they expose, the application owners can also request for services that they to other services. While I of course can appreciate that not all application owners understand how their applications operate over the network, helping application owners define their application via a white-glove service without taking rule ownership is several steps in the right direction.
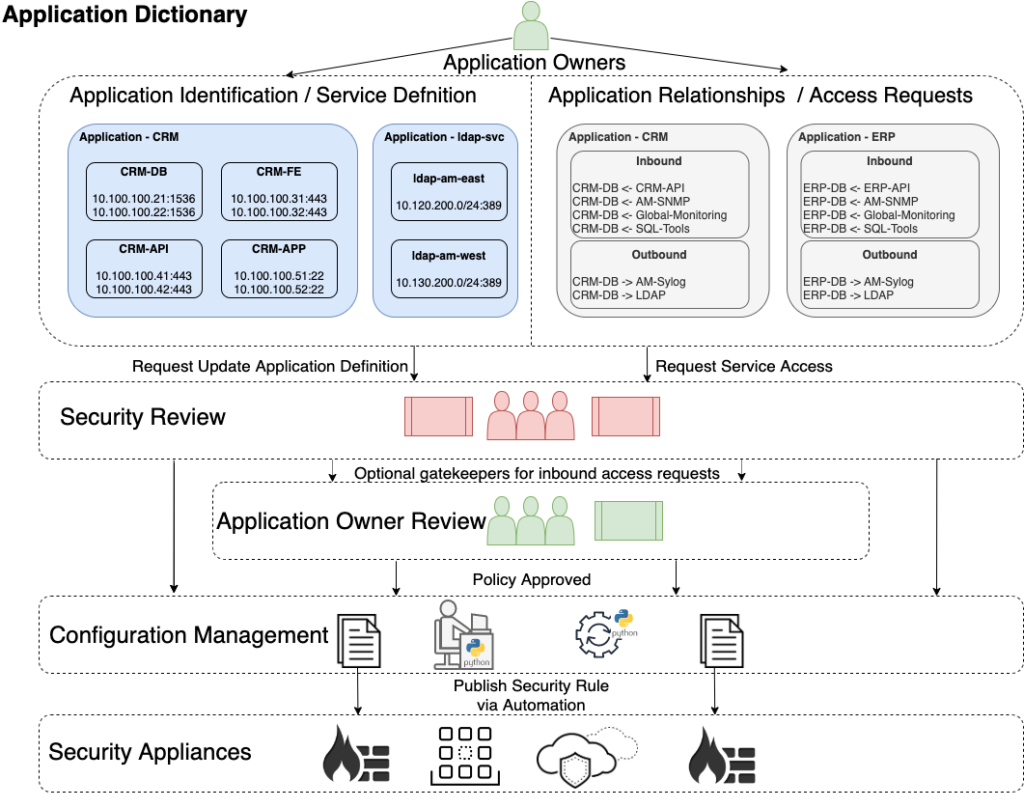
Ok, there is a lot going on here, in the interest of breaking it down to more consumable areas:
Note: Those familiar with Cisco ACI will notice the similarities in terms of naming, such as Application Profiles and Contracts vs Application Services and Application Requests. This is by design, as both solutions are intending to solve similar problems, but the Application Dictionary is only about storing data, regardless of whether or not the traffic is controlled by a networking device or not, such as the case with containers and IP Tables.
To help describe what this system may look like here are two basic wire frames.
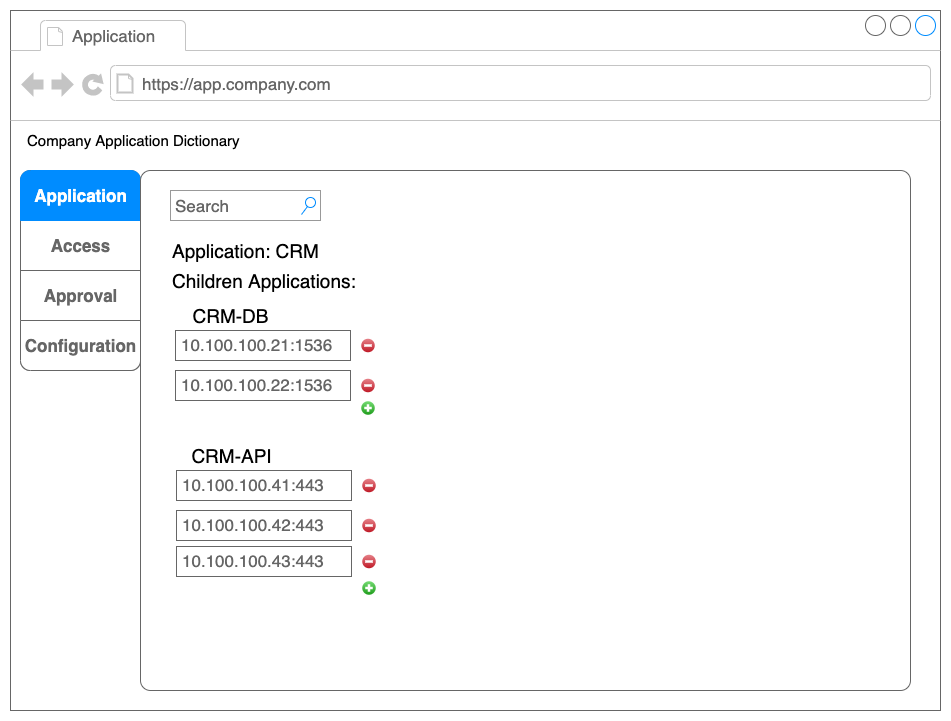
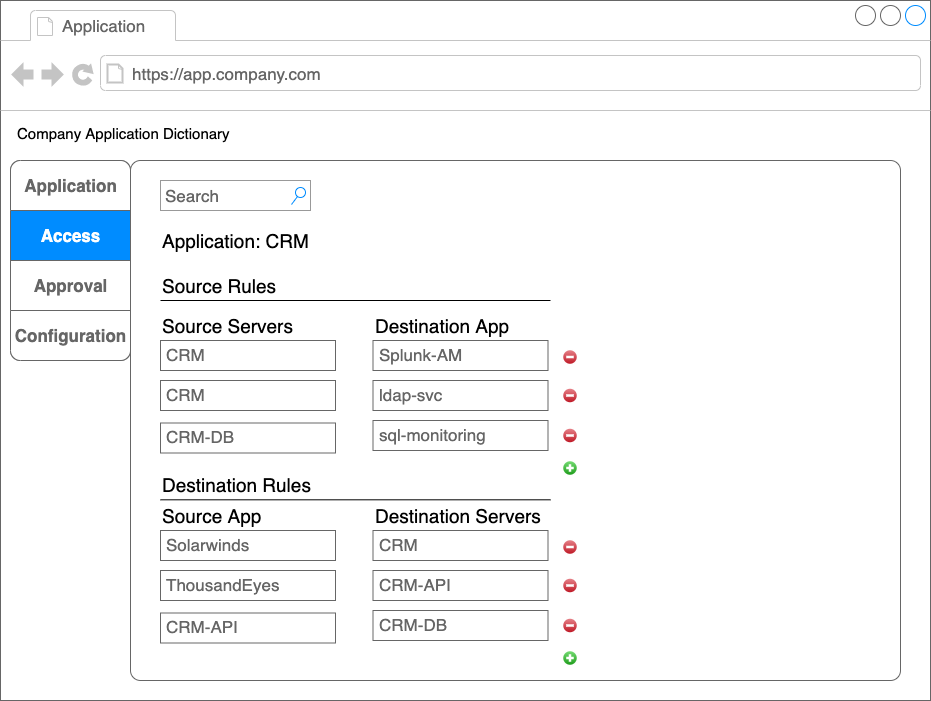
To illustrate these two pieces coming together:
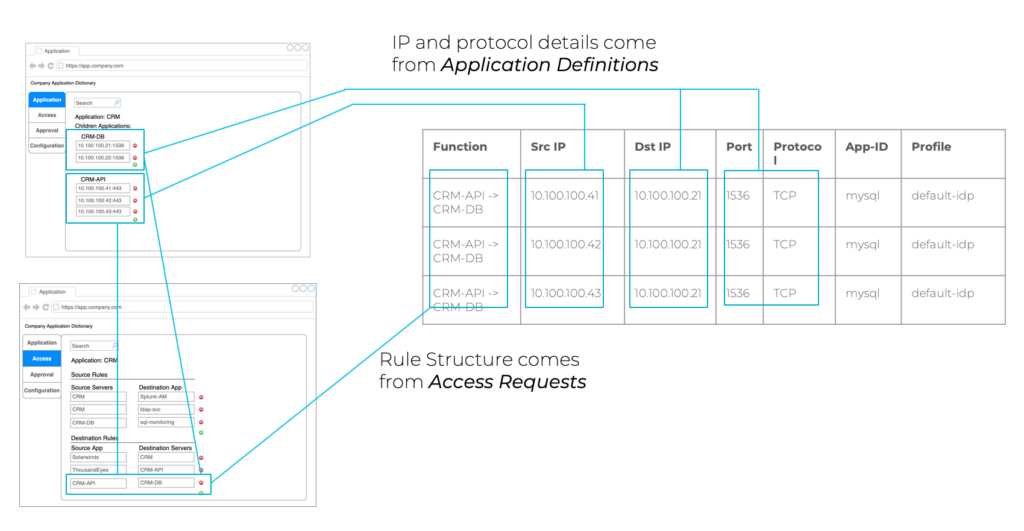
In this simplified example, rule definition and policy creation only follow traditional firewall IP protocol communication patterns. However, this can naturally be expanded upon for many more use cases.
Building such a data model is no easy feat and depends heavily on your environment. Take the following questions an organization would likely have to ask itself before embarking on such a journey:
Since this blog was created, the following demonstrations, presentations, and podcast have been created on the topic.
At NTC, we’ve helped our clients build systems to get them on their way thinking differently about applications, Source of Truth, and application-based intent used to drive network policy and configuration. This is not entirely new ground–such as the aforementioned Cisco ACI–however, it is certainly not well covered ground. There are many things to consider in building such a system, but the power to re-imagine how security is managed can be absolutely game changing for your organization.
-Ken
Share details about yourself & someone from our team will reach out to you ASAP!