Skybox Alternative: Automating Firewall Policy Management with Nautobot + IP Fabric
Skybox’s Closure: A Disruption—or an Opportunity?
Skybox Security’s sudden closure and acquisition by Tufin have left enterprises racing to find a replacement. Uncertainty over service continuity, Tufin’s roadmap, and potential cost increases put IT and security leaders at a crossroads:
- Do you settle for a like-for-like swap with Tufin, inheriting the same legacy challenges?
- Or do you seize this moment to modernize, adopting an automation-first approach that simplifies firewall rule management while enhancing security visibility?
At Cisco Live EMEA 2025, Network to Code and IP Fabric showcased this exact solution—an integrated approach to policy automation and network visibility, eliminating inefficiencies and future-proofing security operations.
A Modern Alternative: Nautobot + IP Fabric
The partnership between Nautobot and IP Fabric offers a future-proof, closed-loop automation solution that goes beyond Skybox’s capabilities. Instead of relying on a standalone tool with inherent data silos, this approach integrates network automation, firewall rule management, and risk-based security insights into a unified platform.
This solution is particularly beneficial for those financial services organizations which must comply with the European Digital Operational Resilience Act (DORA), which requires stringent firewall policy management and audits along with many other mandates. And given the immediacy of the Skybox Solutions closure, this same solution provides a scalable and integrated cybersecurity infrastructure with a fully automated end-to-end workflow for firewall policy rule management.
Key Benefits of the Nautobot and IP Fabric Solution:
- Automated Network Discovery & Visibility: IP Fabric automatically maps your entire infrastructure, providing real-time visibility into devices, configurations, and interdependencies.
- Firewall Rule Automation & Compliance: Nautobot’s Application Dictionary translates high-level application connectivity needs into vendor-neutral firewall policies, reducing errors and simplifying compliance
- Enhanced Security Assurance: With over 160 intent-based checks, IP Fabric continuously validates your network against security policies and compliance standards, proactively identifying vulnerabilities and misconfigurations before they escalate into issues.
- Seamless Policy Management: Nautobot’s Firewall Models application provides a vendor-agnostic framework for modeling Layer 4 firewall policies and access lists. This abstraction simplifies the management of firewall rules across diverse environments, ensuring consistency and reducing complexity.
- Effortless Integration: Nautobot’s and IP Fabric’s open API architecture allows for seamless integration with existing tools and workflows, enhancing data accuracy and operational efficiency.
With this combination, IT teams can reduce complexity, improve accuracy, and enforce security policies dynamically, eliminating the manual burdens that slowed them down with Skybox.
Why Tufin Isn’t the Best Option
Some organizations may consider Tufin as the default replacement for Skybox. But is it really the right move?
Limited Automation: Tufin’s capabilities may not fully support the level of automation required for dynamic, large-scale environments.
Incomplete Visibility: Without comprehensive network discovery, Tufin might leave gaps in understanding the full network topology and device states.
Integration Challenges: Incorporating Tufin into existing ecosystems may require significant adjustments, potentially leading to operational disruptions.
Instead of replacing one legacy tool with another, IT leaders should take this opportunity to adopt a smarter, automated future.
Transforming Firewall Policy Management with Automation
Migrating from Skybox to Nautobot + IP Fabric eliminates the traditional firewall rule request bottleneck that slows security operations today.
The Legacy Firewall Change Process (Skybox & Tufin)
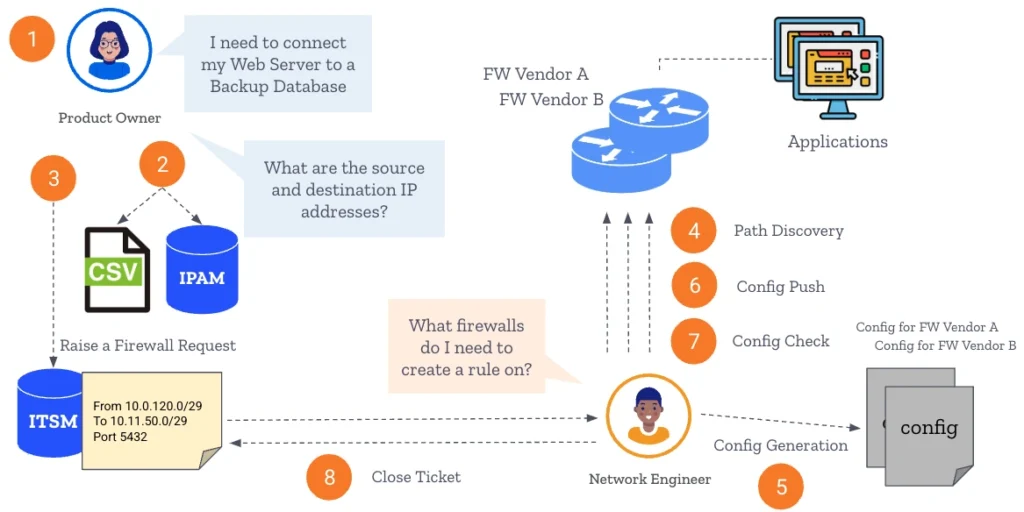
Product Owner (PO) – conducts steps 1 -3 to submit a Change Request (CR) ticket for a new firewall rule—often with incomplete information due to a lack of expertise in firewall management.
Network Engineer (NetEng) – verifies the CR, tracks down missing info, and determines which firewalls are impacted and conducts steps 4 – 8.
4️⃣ Path Discovery & Firewall Impact Analysis NetEng identifies the network path and all firewalls traversed to identify what firewalls need rules changes and what those changes should be.
5️⃣ Firewall Rule Generation- the firewall rules are manually generated for each affected firewall.
6️⃣ Configuration Push – the NetEng pushes each new config to the impacted firewall
7️⃣ Configuration Check – the updated firewalls are checked to verify the traffic flows as requested and rule changes have not created any unintended consequences.
8️⃣ Close Out ITSM ticket – NetEng updates ITSM system and notifies PO that requested changes have been completed
🔥 Final PO Verification & Post-Change Updates – but the process isn’t done yet, the PO is responsible for verifying that the rule works as intended. If any issues are identified, the PO initiates troubleshooting and may re-engage the NetEng for further corrective action.
🛑 Problems with This Process:
- Manual & Time-Consuming: Every step requires human intervention, leading to delays and inefficiencies.
- Error-Prone: Relying on manual path discovery and rule validation increases the risk of misconfigurations.
- Limited Visibility: Engineers lack a centralized view of network and security policies, leading to redundant or conflicting rules.
- Difficult Compliance Auditing: Tracking changes, approvals, and security policy adherence is not streamlined, making audits more challenging.
The Modern Firewall Change Process (Nautobot + IP Fabric)
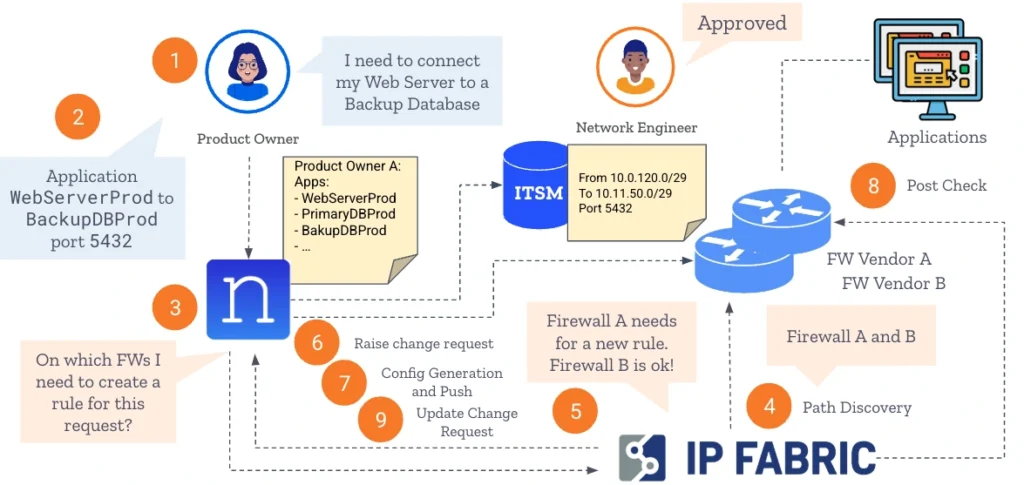
1️⃣ Centralized Policy Management with Nautobot – Nautobot’s Application Dictionary acts as a central repository where the Product Owner can define firewall policies in an abstract, vendor-neutral format, ensuring standardized, consistent rule creation across all applications and firewall vendors.
2️⃣ Policy Definition by the Product Owner (PO) – The Product Owner defines the application connectivity needs, such as connecting WebServerProd to BackupDBProd on port 5432. Instead of specifying firewall rules manually, the PO focuses on defining logical application relationships in Nautobot.
3️⃣ Automatic Firewall Policy Generation – Nautobot analyzes the request and determines which firewalls require rule modifications. This removes manual rule translation and ensures policy consistency across environments.
4️⃣ Network Path Discovery with IP Fabric – IP Fabric automatically discovers the network path between the two endpoints, mapping how the traffic will flow through the network, eliminating the need for a network engineer to manually trace network paths across multiple devices and vendors.
5️⃣ Identification of Configuration Targets – Using network path analysis, IP Fabric identifies the specific firewalls and security enforcement points that require policy updates. In this case, Firewall A needs a new rule, while Firewall B already allows the traffic—ensuring minimal rule changes and avoiding unnecessary configurations.
6️⃣ Change Request Generation & Engineering Review – Nautobot automatically generates a change request (CR) in the ITSM system. A Network Engineer (NetEng) reviews the request to verify policy compliance and security best practices and approves.
7️⃣ Automated Firewall Rule Generation & Deployment – Nautobot automatically generates the configuration for each firewall based on the approved change request and pushes the approved firewall configurations to the relevant firewalls. The new rule is applied consistently across multi-vendor firewall environments.
8️⃣ Verification & Path Validation with IP Fabric – IP Fabric validates the deployed rule, ensuring the firewall changes allow the expected traffic without introducing new risks, guaranteeing end-to-end compliance, security, and network integrity.
9️⃣ Change Logging & Compliance Documentation – Nautobot updates the change request with final implementation details and validation results from IP Fabric and closes out the CR. This ensures all modifications are logged for auditing, compliance tracking, and future reference.
💡 Outcome: With Nautobot + IP Fabric, firewall rule changes are now automated, validated, and fully auditable, dramatically reducing manual effort, errors, and security risks. 🚀
Seamless Skybox Migration: Automate Policy Transfers & Compliance
Migrating from Skybox doesn’t have to be painful—Nautobot and IP Fabric have streamlined the process. With hands-on delivery services and extensive API integrations, Nautobot and IP Fabric ensure a seamless transition—deploying the technology, integrating platforms, and migrating your security policies and firewall configurations with confidence.
🔹 IP Fabric’s discovery engine maps firewall policies and network rules, providing visibility and real-time insights into security configurations before migration.
🔹 Nautobot’s Single Source of Truth (SSoT) App centralizes policy data, synchronizing with Skybox, Tufin, and other security platforms for a seamless transition of policy and configuration data.
🔹 Automated rule validation ensures no policies are lost or misconfigured during the transition.
📅 Schedule a Demo to see how Nautobot and IP Fabric can replace Skybox while advancing your security and automation strategy.
Conclusion
Final Thoughts: Future-Proofing Your Security Strategy
Skybox’s closure isn’t just an inconvenience—it’s an opportunity to modernize. Instead of migrating to another static, legacy tool, IT leaders can future-proof their network security with automated policy management and full network visibility.
🔗 Migrate from Skybox Today. Future-proof your firewall automation with Nautobot + IP Fabric. Book a live demo now.
Contact Us to Learn More
Share details about yourself & someone from our team will reach out to you ASAP!
